A while back, Jeff Atwood wrote about the “maximize” behavior in Windows and Mac OS. The subject: There’s a button on the top-right of each window in Microsoft Windows that resizes the window to fill the screen. There’s a green button on the top-left of each window in Mac OS with a + on it, that Windows users often think will cause the window to fill the screen, but it actually resizes the window to its “best size”. Apple calls this Zoom.

In my experience, MS Windows users hate the Mac way of doing things, and Mac users hate the Windows way of doing things. The comments on Jeff’s post reinforce this impression. I have often wondered why this little difference causes such strong reactions. I’m pretty sure it has to do with the taskbar/dock.
In MS Windows, each window has an associated button on the taskbar1. These buttons stay in the same order2 and in the same place3. This means that no matter what you do to a window, whether you maximize, minimize, resize, or move it, there is always a part of the window showing: the taskbar button. No window can ever be completely hidden. You can get to every open window with a single click. And since the buttons are always in the same place, you can use spatial relationships to remember which window is which, in addition to the icon and text label on each button. So, Windows users like to maximize windows, because you get the maximum amount of screen space for the program you’re using, but navigating between windows is still fast and easy.
In Mac OS X, that isn’t the case. There is no button on the toolbar for a window (only entire programs, which often have multiple windows). Windows can be completely hidden behind each other. Then, if you want to see one of the windows that isn’t on top, you have to move all of the windows above it. Since this is the case, users have to take it upon themselves to ensure that they can always see a piece of each window. This results in not wanting to maximize any windows. If they do that, all of the other windows will be completely hidden and it will be a lot of work to navigate between them.
Recent versions of Mac OS X have a feature that is an attempt to work around this limitation: Exposé. Press a function key (or move your mouse pointer to a specific corner of the screen) and all of your windows shrink down to thumbnail views so you can click on the one you want. This works fairly well if you a) don’t have many windows open, and b) are using windows that look distinctive from one another. But, if you have so many windows open that each one is tiny, it doesn’t help you much. Similarly, if you have 10 windows open from each application, you can’t tell which one you want by looking at thumbnails of them. Here’s what a Windows Exposé clone might look like on my desktop if I’m working on a programming project:
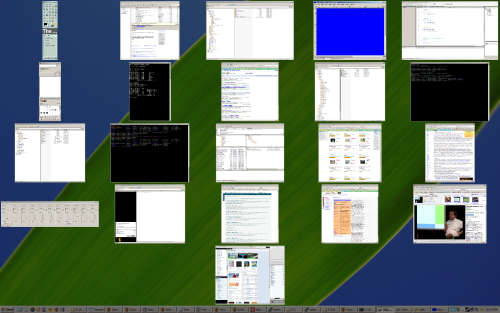
As you can see, the windows are so small that it’s hard to make out what is on each one, unless it is something distinctive like the video in the bottom right corner. Also, a number of windows look the same, so if I want to find that one command prompt window, which of the black squares do I click on?
But even if these problems didn’t exist, Exposé would still be more work to use than clicking on windows in the taskbar. The taskbar requires only one click, Exposé requires either a mouse move to a corner or a keyboard button press, plus a mouse click.
Of course, the Windows taskbar isn’t perfect either. Once there are enough windows open, there is almost no text on each taskbar button, so you can’t tell different windows from the same application apart.
Even so, I still think the Windows maximize button is way better than that stupid zoom.
Footnotes
- Unless you use the default “Group similar taskbar buttons” setting in Windows XP and later. back
- Except in Windows Vista where the buttons rearrange themselves to group windows from the same program together. back
- They shrink and grow to accommodate more and less buttons, changing their size and absolute position somewhat, but the relative positions of the buttons to each other are maintained. back